Thoroughly securing your IT landscape has become more and more important over the last couple of years. With an increase in (user) data to be managed, processed, and stored, encryption of this data should be on your agenda towards fully secured IT infrastructure.
Therefore, we will look at how to leverage LUKS encrypted storage on OpenStack to encrypt volumes at rest in this tutorial. We will look at two ways of defining and using encrypted volumes in OpenStack: via web interface and via OpenStack CLI. Let’s start with the web interface.
Prerequisites
To follow along with this tutorial on NWS OpenStack, you will need an NWS ID. You will also need to create an OpenStack project in which you can create volumes and compute instances. If you want to follow along in your terminal, you will additionally need to download the OpenStackRC file for your project. If you need a recap on how to go about this, see our tutorial on starting a project and creating a server (you will need one later) on NWS.
Configuring LUKS Encrypted Storage on the Dashboard
First, let’s see how you can provision LUKS encrypted volumes in Horizon, OpenStack’s web interface. If you’re an NWS customer, you can access Horizon either at https://cloud.netways.de and login with your NWS ID, or by clicking the “Go to App” button in the top right of your OpenStack project’s overview page at MyNWS.
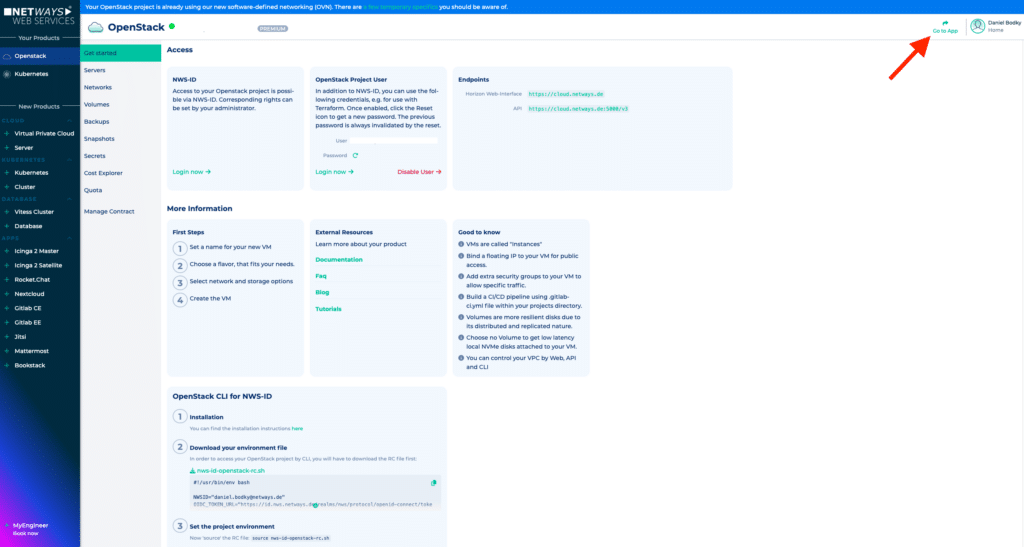
Navigate to OpenStack Horizon from the MyNWS dashboard
Creating a New LUKS Encrypted Volume
Once you made it to the Horizon dashboard, navigate to Volumes > Volumes and click on Create Volume in the top right. A form will open for you to specify the desired settings. You can configure the following settings here:
- Volume Name – make sure to choose a meaningful name for your volume here, e.g.
encryption-tutorial-volume - Description – add information regarding this volume here if needed
- Volume Source – you can choose between creating an empty volume here or import an existing image
- Type – this is the most important setting, as this will define whether your volume will be encrypted or not – more infos below
- Size – the desired size of your volume
- Availability Zone – where you want OpenStack to store your volume; in NWS OpenStack, there’s only one availability zone (nova)
- Group – add your volume to a preexisting volume group if needed
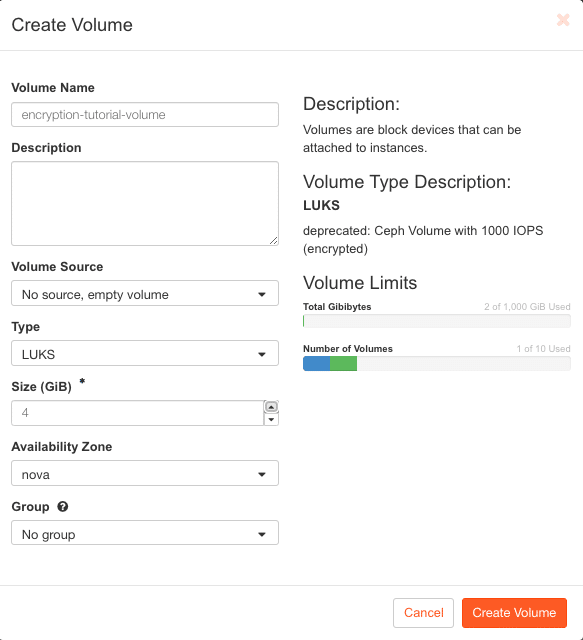
Exemplary configuration of a LUKS encrypted volume in NWS OpenStack
In the screenshot above, I configured a volume to use the LUKS type, which is the volume type for LUKS encrypted storage on NWS OpenStack. I also made sure to create a new, empty volume and set the size to 4GB.
If you are following along on an OpenStack environment that isn’t NWS OpenStack, the volume type might be named differently.
Once you’re satisfied with your volume configuration, click on Create Volume. After a few moments, OpenStack will have provisioned the new, encrypted volume for you. Next, you need to attach it to a compute instance.
Using LUKS Encrypted Volumes
A volume alone won’t get you far, no matter if encrypted or not – you need a client consuming it. For this tutorial, this will be a simple compute instance. Deploy a new server via the NWS OpenStack dashboard or by navigating to Compute > Instances in OpenStack Horizon and clicking on Launch Instance in the top right.
Once the server is up and running, attach the encrypted volume via the OpenStack Horizon dashboard: Expand the dropdown in the Action column of your server’s listing, and choose Attach Volume from the available actions.
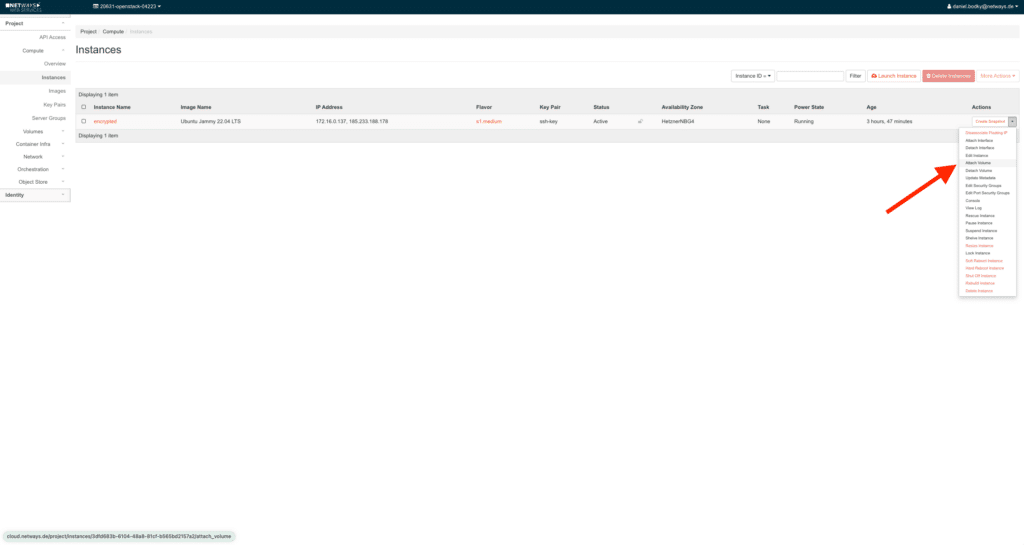
Another popup dialogue will open, prompting you to choose the volume to attach from a dropdown of available volumes. Pick the LUKS encrypted volume you created before and confirm by clicking on Attach Volume:
That’s it – you attached encrypted storage to your server. If you log into the server (e.g. via SSH), you see a new storage device (probably /dev/sdb). You can use it like any other volume, OpenStack already decrypted the block storage for you.
This is a good moment to emphasize again that your LUKS encrypted volumes are only encrypted at rest, not in transit – keep that in mind when reasoning about your security posture!
Configuring LUKS encrypted storage in the Terminal
If you prefer a terminal and Openstack’s CLI over its dashboard, there is of course another way to provision LUKS encrypted storage on OpenStack. Make sure you have your OpenStackRC.sh at hand, source it, and pick the project to work in, if prompted:
source ~/Downloads/nws-id-openstack-rc.sh Testing authentication and fetching project list ... Please select one of your OpenStack projects. 1) aaaaa-openstack-bbbbb 2) ccccc-openstack-ddddd 3) eeeee-openstack-fffff 4) ggggg-openstack-hhhhh 5) iiiii-openstack-jjjjj 6) kkkkk-openstack-lllll 7) mmmmm-openstack-nnnnn 8) ooooo-openstack-ppppp Enter a number: 1 Selected project: aaaaa-openstack-bbbbb
With the correct project picked, you can proceed to create your encrypted volume.
Creating a New LUKS Encrypted Volume
First, you need to identify the storage type providing LUKS encrypted storage in your OpenStack environment. You can list all storage types available to your OpenStack project with this command:
openstack volume type list +--------------------------------------+--------------------------+-----------+ | ID | Name | Is Public | +--------------------------------------+--------------------------+-----------+ | 2f487bd6-628d-46ba-83c5-21c6dbb4c67d | Ceph-Encrypted | True | | e0704085-2e47-4e3d-b637-ae04e78f5000 | Ceph-Encrypted-High-IOPS | True | | 21b793e6-8adf-4c92-9bf9-14f5a7b6161a | LUKS | True | | 664b6e93-0677-4e11-8cf1-4938237b6ce2 | __DEFAULT__ | True | | 0a65e62f-3aad-4c6d-b175-96dedaa7ba1f | Ceph-High-IOPS | True | | c4a685b0-64c4-4565-9b4c-9800056d659d | Ceph | True | +--------------------------------------+--------------------------+-----------+
On NWS OpenStack, the storage type providing LUKS encryption is conveniently called LUKS. Next, you will have to create a new volume, referencing the identified volume type:
openstack volume create --type LUKS --size 4 encryption-tutorial-volume +---------------------+------------------------------------------------------------------+ | Field | Value | +---------------------+------------------------------------------------------------------+ | attachments | [] | | availability_zone | nova | | bootable | false | | consistencygroup_id | None | | created_at | 2024-03-04T12:41:29.000000 | | description | None | | encrypted | True | | id | 9b20a1d8-bfb6-4e4f-bb4b-dbda62e4afc7 | | multiattach | False | | name | encryption-tutorial-volume | | properties | | | replication_status | None | | size | 4 | | snapshot_id | None | | source_volid | None | | status | creating | | type | LUKS | | updated_at | None | | user_id | acfef1ea27ec3ac25fa5009238cdeb2cc5ae2c943da7ecb279c43a5a91b8a4bf | +---------------------+------------------------------------------------------------------+
In the example above, I created a volume encryption-tutorial-volume with a size of 4GB. Next up, you will want to attach the volume to a VM.
Using LUKS Encrypted Volumes
In order to consume the volume, you will need a server to attach it to. Create a new server using the following command, or deploy one via the NWS or OpenStack dashboards:
openstack server create --flavor s1.small --image "Debian 10" --network public-network test-server
This command will work in any NWS OpenStack project – if you’re following along on a different OpenStack environment, you might have to adapt the referenced flavors, images, and networks.
Once the server has come up, you can go ahead and attach the LUKS encrypted volume you created before:
openstack server add volume --device /dev/sdb test-server encryption-tutorial-volume +-----------------------+--------------------------------------+ | Field | Value | +-----------------------+--------------------------------------+ | ID | 9b20a1d8-bfb6-4e4f-bb4b-dbda62e4afc7 | | Server ID | 7952e17d-0781-41c3-a1e9-b758574ac336 | | Volume ID | 9b20a1d8-bfb6-4e4f-bb4b-dbda62e4afc7 | | Device | /dev/sdb | | Tag | None | | Delete On Termination | False | +-----------------------+--------------------------------------+
If you log into your server now (e.g. via SSH), you should see a new storage device /dev/sdb. You can go ahead and format, mount, and consume it like any other OpenStack volume. OpenStack will have decrypted the block storage for you in the background already.
Summing it up
OpenStack provides you with everything you need to encrypt your storage at rest. You can use either OpenStack’s Horizon dashboard or its CLI to create, encrypt, and attach block storage volumes, without having to change any configuration on your VMs.
The feature comes at very little additional cost (OpenStack stores the encryption keys as Secrets in Barbican, OpenStack’s key manager, which incurs a small, fixed cost per secret in NWS OpenStack), and is a ‘quick win’ in terms of security posture.