Kubernetes impresses us with its flexibility and scalability and has now become the standard for modern container orchestration. It enables you to deploy and scale applications efficiently and operate them with high availability. But with great performance comes great responsibility: security vulnerabilities in Kubernetes can have serious consequences – from data loss and system failures to compliance violations. In this article in our series, we will show you the key points of attack in a Kubernetes cluster, why they are so critical and how you can improve the protection of your infrastructure in the long term with specific technical measures.
Why Kubernetes security is important
Kubernetes itself is robust, but the complexity of its architecture opens up various attack possibilities for attackers. Containers, pods, nodes, APIs – every component can become a gateway. A small security error can quickly affect the entire cluster. A proactive approach to security is therefore essential.
Kubernetes security refers to a series of measures taken to protect Kubernetes and the applications running on it from attacks, unauthorized access and data misuse.
As the leading container orchestration platform, Kubernetes offers many features that can improve the security of the applications running on it, including role-based access control (RBAC) and pod security policies. However, it is essential to take additional security measures to protect the platform itself.
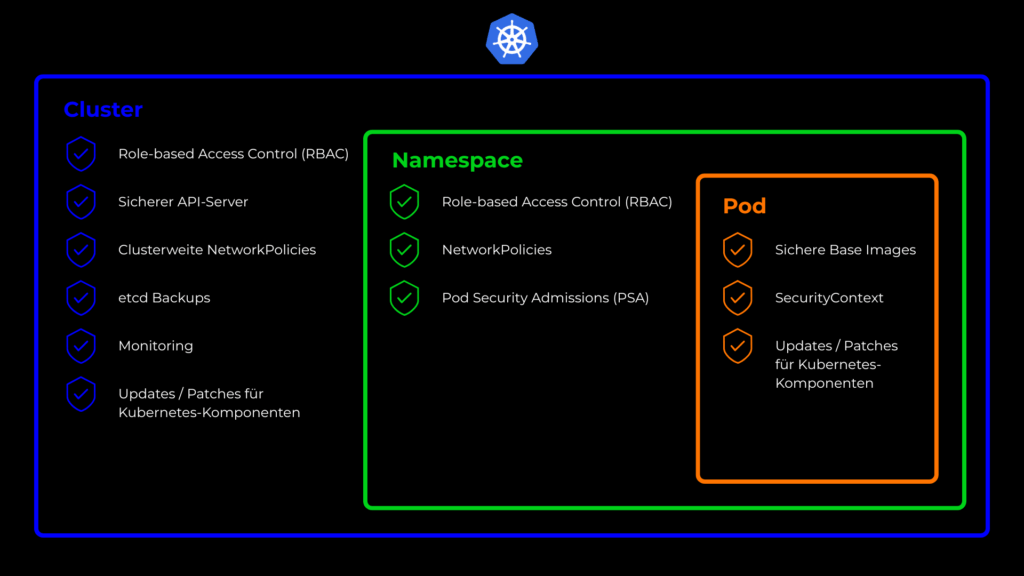
Typical points of attack in Kubernetes
1. insecure API access
The Kubernetes API forms the heart of your cluster. The so-called kube-apiserver is the central control unit of the cluster. Anyone who has access to it can control almost everything. It receives all commands, distributes them to the relevant components and keeps the overall status of the system up to date. However, insecure configurations, unprotected tokens or a lack of role restrictions offer attackers an easy game. If the API server is compromised, it is not just individual databases that are at risk, but potentially the entire cluster.
2. missing role and authorization concepts
Without Role-Based Access Control (RBAC), users or services can access resources that they do not need or should not see. This greatly increases the risk of data manipulation or unauthorized access. If an attacker gains access to the cluster, they also have access to everything.
In addition, administration interfaces such as the Kubernetes dashboard, Rancher or ArgoCD should never be publicly accessible. If these are inadequately secured, they offer attackers direct access to administrative functions.
3. insecure container images
Containers are based on images. Outdated or unverified images may contain malware or known security vulnerabilities. As soon as a container is started, your cluster is potentially at risk. Even if containers generally run in an isolated environment, they can be compromised by vulnerabilities in the container runtime or by insecure base images.
4. network security vulnerabilities
Another critical point is the network architecture. By default, pods often communicate freely with each other. Without network policies, attackers can operate laterally within the cluster as soon as they have found an access point. This means that they move from a compromised container to other components. Lack of isolation between different environments (such as production, development and management networks) significantly increases this risk.
5. missing updates and patches
Kubernetes and its components are developing rapidly. The new updates and patches contain important elements that close security gaps, among other things. Unpatched nodes, API servers or plugins are a popular target for attacks.
Protective measures for your Kubernetes cluster
1. securing the API
Secure the Kubernetes API by restricting access to authorized users and ensuring that communication with the API is encrypted.
- Use TLS for all API connections.
- Use strong authentication methods (e.g. OIDC or short-lived certificates).
- Restrict access via firewall rules and IP whitelisting.
2. role-based access control (RBAC)
Use RBAC to grant users and services access only to the resources they need to perform their tasks. This can minimize the risk of unauthorized access.
- Define precise roles for users and services.
- Only grant the minimum necessary rights (least privilege principle).
- Check regularly whether authorizations are still correct.
3. secure container images
Scan container images for vulnerabilities and ensure that only trustworthy images are deployed in the cluster. Use tools to ensure the integrity of the images.
- Use trustworthy sources for images.
- Scan images regularly for vulnerabilities (e.g. with tools such as Trivy or Clair).
- Keep images up to date and remove unnecessary packages.
4. implement network security
Configure NetworkPolicies to control traffic within the cluster and between the cluster and external networks. Use firewalls to block unauthorized traffic and monitor network traffic for suspicious activity.
- Use NetworkPolicies to control the communication between pods.
- Segment the cluster according to security zones (e.g. frontend vs. backend).
- Monitor network traffic for anomalies.
5. regular updates and monitoring
Pay attention to the latest updates to keep the cluster up to date. Also use tools that help you to track security incidents and set up a monitoring system.
- Patch Kubernetes components regularly.
- Implement monitoring and logging to detect attacks at an early stage.
- Use tools such as Falco, Prometheus or Grafana to monitor security incidents.
6. protection of the etcd memory
etcd is the primary data store of the Kubernetes cluster and securing it is critical. Implement encryption, authentication and access control here to protect etcd from unauthorized access.
- Close all communication channels
- Introduction of an authentication procedure.
- Restrict access to trusted sources.
7. training of users and administrators
Educate users and administrators on Kubernetes security best practices and policies to minimize the risk of human error or security incidents caused by negligence or lack of awareness.
- Set clear guidelines for dealing with Kubernetes and Kubernetes security.
- Ensure that the relevance of security measures resonates with users.
- Set regular training dates.
Conclusion: A holistic security concept is needed!
Kubernetes security is not a one-off process, but a continuous security cycle. If you know the typical points of attack and implement targeted protective measures, you can effectively secure your cluster and minimize risks. By consistently using TLS, precise RBAC and network policies, security profiles for containers and securing critical administration and communication channels, you can lay a solid foundation against a wide range of attack vectors. Security in the cluster also means stability, compliance and trust in your applications.
Remember: security measures must be continuously reviewed and adapted to the constantly changing threat situation. So stay on the ball and don’t be afraid to integrate new approaches and technologies into your security strategy.
If you want to further simplify your Kubernetes experience, it’s worth taking a look at Managed Kubernetes offerings. We take care of many security aspects such as updates, patches and monitoring so that you can focus on developing your applications – without compromising on security, network security and etcd backups.





0 Comments